 Overview
Overview
In the field of Identity & Access Management (IAM), complexities are managed through multiple layers of abstractions such as policies, roles, and entitlements, which are critical for orchestrating interactions across different business units. For these abstractions to be effective, they must be accurately labeled to ensure that business users can fully understand the associated security implications. As noted by Phil Karlton, ‘There are only two hard things in Computer Science: cache invalidation and naming things.‘ In practice, these labels often fail to precisely represent their contents and may quickly become outdated in our dynamic technological landscape.
This problem can be addressed through the integration of an Identity Knowledge Graph, Attribute-Based Access Control (ABAC), and advanced Data Science technologies. These tools work together to refine and update the representations of IAM elements, ensuring they remain relevant and understandable, thus enhancing overall security governance.
Approach
In almost all engineering disciplines, artifacts developed to represent a concept (conceptual artifacts) are very different than the artifacts of its eventual realization (applied artifacts).
Examples:
– A programmer uses multiple abstract layers to manage complexity, which a compiler later simplifies for performance.
– A civil engineer works with detailed blueprints and models, which differ significantly from the final structure.
Is there a possibility of simplifying IAM abstractions “while in-use” to an attribute-driven rules, such that decision maker can comprehend the implications intuitively and/or system can compile them into native permissions that can be efficiently enforced?
Solution
ABAC is a flexible access control approach that can implement policies which are limited only by the computational language and the richness of the available attributes – NIST Publication 800-162.
According to NIST Special Publication 800-162, any access control policy can be articulated through attributes, hence it can form as a basis for expressing simplified, understandable application security policy while in use. This process replaces complex abstractions (roles, policies, coarse grained entitlements) with more straightforward, attribute-driven rules.
The system supports various ABAC policy expressions to accommodate different complexity levels. These expressions are machine interpretable and would be used to deduce natively enforceable permissions and policies.
Business users can often understand ABAC policy expressions as they are. If necessary, these can be translated into plain language using Large Language Models (LLMs).
A critical aspect of this system is the comprehensive mapping of identity domain entities—from users to permissions (resources, actions)—along with their attributes and the accuracy of this data, known as Identity Knowledge.
Due to practical constraints, only a subset of the Identity Knowledge is available for any given application/system. Applications are classified by the extent of information available. Application can progressively elevate itself through these classes as the system gains more information over time. Those with more comprehensive Identity Knowledge would have more simplified policy expressions.
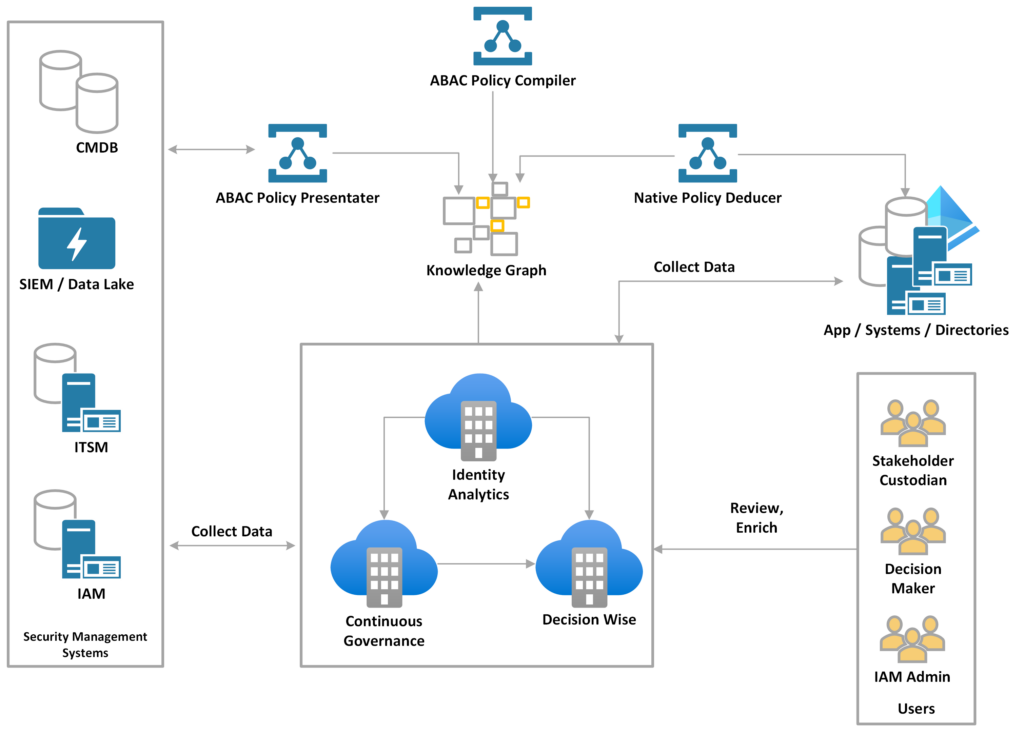
The outcome is a continuously evolving system that simplifies access control policies based on available information, enabling intuitive understanding of security implications by business users and more efficient policy enforcement.
At Vivid Computing, we have successfully implemented such solution for Platform Resources. For more information, please visit ABAC for Platforms.